One of the big challenges blockchain technology faces as an industry is generating enterprise adoption with sufficient security measures in place. Aleph Zero is solving that problem with a very methodical approach.
Aleph Zero was born nearly four years ago to build a new consensus protocol and eventually its own blockchain system, cofounder and COO Antoni Zolciak said. Unlike many companies who are in a rush to get to market, Aleph Zero started with a focus on developing the proper scientific fundamentals with audited and peer-reviewed research papers. They also established the Aleph Zero Foundation, which oversees the intellectual property and platform development. Cardinal Cryptography develops customized implementation of Aleph Zero technology.
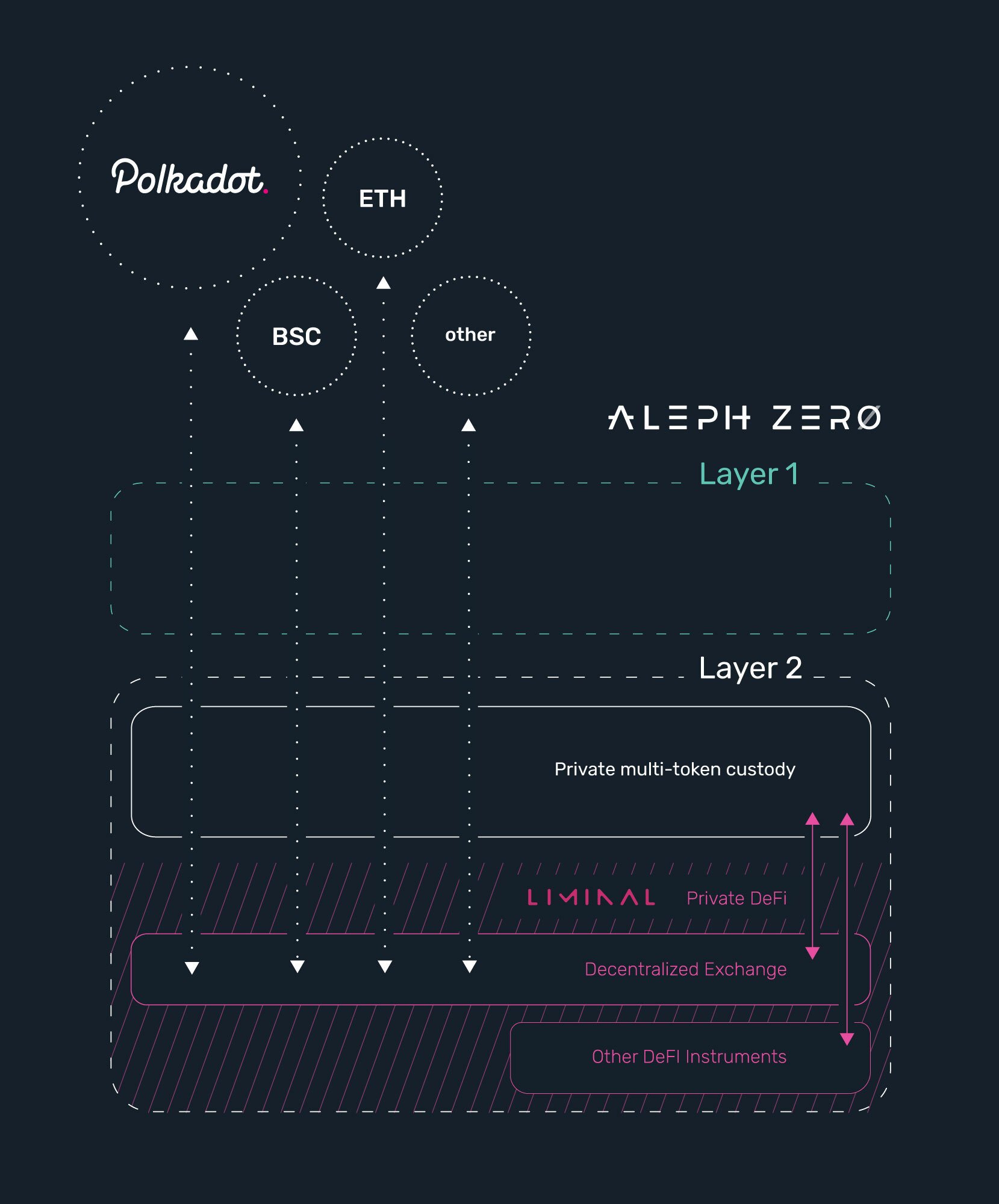
The first product is a Layer 1 infrastructure which is based on a directed acrylic graph (DAG) platform and offers scalability and speed. It is a public blockchain with private smart contracts. That combination allows users to gain enough trust in the core environment so they are not wary of using a public blockchain.
The second is Liminal, a Layer 2 multichain privacy layer that is a plug and play solution for those building dApps with privacy features.
The final one, Common, is a user-centric DEX that prevents front running by utilizing the privacy features of Liminal.

Co-founder and CEO Matthew Niemerg, Ph.D. said one key issue Aleph Zero addresses is the miner extraction value problem, where any validator can generate value by changing the transaction order before finalizing or committing them to the blockchain.
“One of the things we’re focusing on is by using different levels of cryptography to solve the miner extraction value problem; this is done by encrypting transactions and finalizing the order while the transactions are still encrypted and then decrypting the transactions after the order is determined prior to the execution of the transactions,” Dr. Niemerg said. “What this basically allows is for these people who are running validators or running miners to not necessarily know what that transaction is supposed to do. All they know is that here’s an encrypted transaction and the order of encrypted transactions. Once the order is finalized, the transactions are decrypted and if the transaction is valid, the state transition is applied, or in other words the transaction is executed. ”
Matthew Niemerg.“When solving the miner extraction value problem, we want to limit the information validators have about the actual transactions. Their role is reduced to ordering transactions. During the execution stage, if a decrypted transaction is valid, then the update to the underlying state is applied”.
Liminal allows users to perform private transactions on both local states and global ones, he added.
Say a company wants to use private data for training machine learning models, Dr. Niemerg said. Each participant can do their own share of the computations and have them aggregated so a final comprehensive value can be used for the bootstrap. Then, new data can be fed into these machine learning models to test how well these new results perform against trained ones. Alternatively, one can also perform private calculations of real-time data that a company doesn’t want to disclose using public training sets. Companies can keep their data private while still connecting it to larger ecosystems.
That capability has been cited as being able to foster collaboration between corporate competitors uniting to solve global issues like vaccine research. Dr. Neimerg said there are other ways of using blockchain as a data availability layer where you don’t have to store an actual file on a distributed ledger. What you can instead do is store the hash and metadata related to the server and use a mathematical technology that has been around for more than a half-century.
Erasure codes have been used in the mathematics world for decades in such applications as the space program and CD-ROM technology, Mr. Neimerg explained. This concept has been applied to RAID (redundant array of independent discs), but you can take the notion a step further and instead of locating all the discs locally you locate them across multiple data centers. Yes, there is added latency but also more resiliency in case one data center goes offline. Private companies can take advantage of multiple data centers so if a hacker penetrates one, the upside is that the hacker will only find random data.
In order for blockchain to reach its full potential, enterprise adoption is a must. Solving trust concerns about public networks is one task but there is another, Dr. Niemerg said. The industry must actually start working on the problems they keep saying blockchains can solve. For a while there was plenty of talk about its effectiveness with global remittances, for example, but for the longest time, few were offering remittance services, presumably due to regulations.
“The time difference between talking about the potential of the technology and bringing products to market is starting to converge a lot faster which I think is an important point,” Mr. Niemerg said. “There’s also this notion that it’s going to change the world and of course it can; and it’s going to be transformational but it’s still going to take awhile to get there.”
“There are some nuances whenever you start moving into this permissionless aspect ( permissionless being primarily these public infrastructures), but, for the most part, most of the basic underlying security models are translated into this new paradigm and you don’t have to deal with a lot of creation of brand new technology or terminology… a lot of it is repackaged and repurposed but under a slightly different security model.”
“That’s not necessarily terribly disruptive, that’s evolution,” Dr. Niemerg concluded.
More about Blockchain
Best Universities Offering Blockchain And Crypto Degrees